Levels of identity security and groups of secure features (2020)
Innovative and sophisticated security printing solutions leveraging security features, advanced technologies, and unique materials lay the foundation for document security.
Simply stated, they reduce the risk of the card or holder data being altered, copied or reproduced.

There's more.
Identity documents with an elaborate design are the pride of both the country and the citizens and are immediately recognized as trustworthy evidence of identification.
Let's dig in.
Document security features: goals
Security features can help in verification by providing intuitive and easy to verify elements that are visible with the naked eye or by touch (tactile effects) and which protect both the document structure and personal data.
The objective is to help an Immigration or Border Control Officer to answer two main questions. The third one can be answered by fingerprint matching or facial recognition.
Is the document genuine?
Is the citizen's data authentic?
Is the person present the true owner of this document?
So what are we talking about?
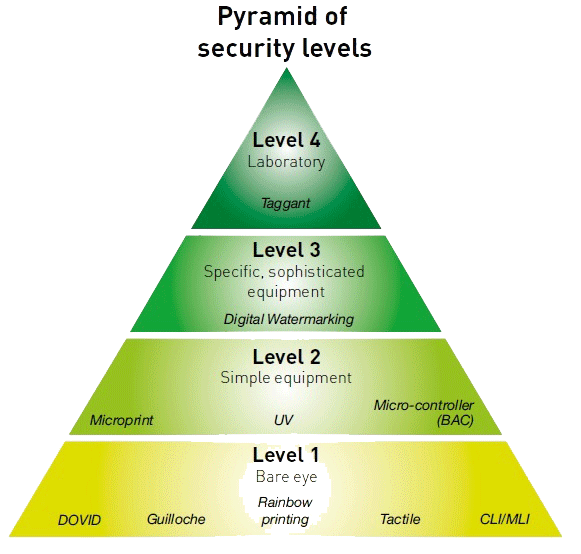 ID levels in the security printing industry
ID levels in the security printing industry
Levels of Identity Security
Four recognized security levels that can be implemented in identification documents.
It sounds simple. And it is.
Level 1 Security
The first level (overt) relates to security features that can be easily checked by the public (in KYC checks, for example) without special aids.
Level 2 Security
Second-level (covert) relates to security features that can be checked with simple aids, such as magnifiers and UV-lamps.
Level 3 Security
Third-level (forensic) security features are for qualified forensic laboratories and other sophisticated laboratory equipment.
Level 4 Security
The fourth security level is secret and includes safety measures known only to a narrow range of experts in many cases the manufacturer only.
Level 1 document security features: your front door key
The main principle of these security features is that fraud will preferably be detected at level 1- with the naked eye – and with close attention paid to alteration of personal information.
Watch some of our features on level 1 and Level 2 in our video.
The document is also protected against counterfeiting following the same principle.
Gemalto is highly experienced in security design and will propose, per customer requirements, a solution that delivers maximum protection against forgery, counterfeiting, and unlawful personalization.
The documents will also be manufactured with the use of directly applicable techniques that are highly effective in this respect.
Three groups of security features
Three groups of security features can be implemented:
1. Security Features that are difficult to copy
Security printing
Optically variable features
Non-printed security - elements such as holograms and surface structures
2. Security Features that are difficult to produce
Security printing
Optical effects
Surface structures
3. Technologies/materials that are difficult to come by
Certain printing technologies
Security paper
Special holograms
Special high-security inks
Digital security: the 5th dimension
Digital security is the 5th level we did not mention earlier. It's a dimension unseen by the naked eye but real.
Think about this for a moment.
Electronic identity documents such as national ID cards or ePassports equipped with a microprocessor and secure applications offer an additional dimension of security to the physical features.
Why?
It is because secured digital data is virtually impossible to alter and allows reliable automated verification and easy machine readability.
 The micro-controller included in the passport, for example, represents a highly secure feature in itself.
The micro-controller included in the passport, for example, represents a highly secure feature in itself.
The best part?
In the case that a counterfeiter successfully manages to change the portrait and citizen information on the data page, the data in the chip cannot be accessed and altered.
Any tampering attempt can be detected since the altered data will not compute correctly, as it has not been signed and authorized by the Issuing Authority.
If fingerprints are stored in the chip, a simple biometric matching can be done to verify the document to the person presenting it.
Smart security features
Use of the latest cryptography to secure the data
In-house developed end-to-end applications
Biometric data for secure identification
Highest level of privacy and security
Confidential communication by contact or contactless, or both (dual interface)
Secure application features
Secure data storage, identification, authentication, and digital signature
Protection by PIN or biometric authentication
Multi-usage of electronic cards for identification, travel, payment and much more
Automated verification
Yes, you've got it.
Security features and the microprocessor in the card or passport can create a powerful combination to authenticate the document and the holder's data.
Where do we fit?
Thales has a background of secure government printing dating back to 1886 with the acquisition of Setec, formerly Finland's National Printing House in 2005.
 Level 2 security feature: UV ink – here you can see the edge of a passport under ultraviolet light.
Level 2 security feature: UV ink – here you can see the edge of a passport under ultraviolet light.
Printing expertise includes banknotes, stamps and identity documents with a long track record in innovation.
Thales has five certified security printing sites worldwide (ISO 14298 INTERGRAF).
As a result, the company can offer clients unrivalled business continuity and global supply chain integrity for the production of a wide range of innovative documents, including ePassports and eID cards.
Typically, Thales works together with its client's security features experts to make the best possible selection of features to match the client's needs.
The goal is that the product and its authenticity can be indisputably trusted.
This goal is achieved by using technologies that make documents impossible to copy, using several different techniques, using each technology at the highest available quality and level, and using rare means and materials with limited availability.
In other words, Thales uses technologies and materials that are difficult to copy, difficult to use, and challenging to come by.
